| .circleci | ||
| .github | ||
| docs/images | ||
| src | ||
| .gitignore | ||
| .gitmodules | ||
| LICENSE | ||
| README.md | ||
| SECURITY.md | ||
| THANKS.md | ||
Community Edition
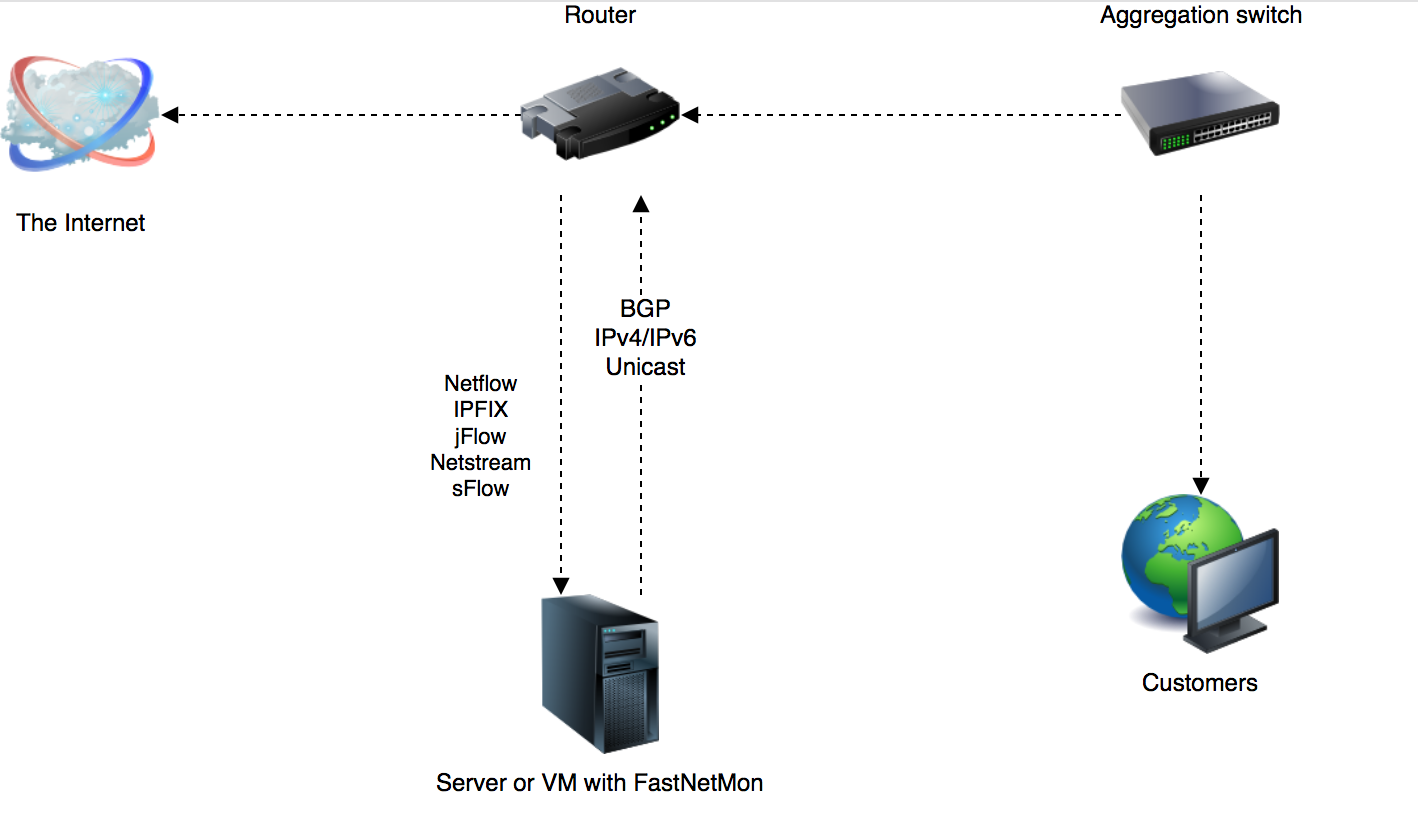
FastNetMon - A high performance DDoS detector / sensor built on top of multiple packet capture engines: NetFlow, IPFIX, sFlow, AF_PACKET (port mirror).
What do we do?
We detect hosts in the deployed network sending or receiving large volumes of traffic, packets/bytes/flows per second and perform a configurable action to handle that event. These configurable actions include notifying you, calling script or making BGP announces.
Legal
FastNetMon is a product of FastNetMon LTD, UK. FastNetMon ® is a registered trademark in the UK and EU.
CI build status
Project
🌏️ Official site
⭐️ FastNetMon Advanced, Commercial Edition
🌟️ FastNetMon Advanced, free one month trial
📜️ FastNetMon Advanced and Community difference table
📘️ Detailed reference
🔏️ Privacy policy
Supported packet capture engines
- NetFlow v5, v9, v9 Lite
- IPFIX
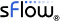 v5
v5- PCAP
- AF_PACKET (recommended)
- AF_XDP (XDP based capture)
- Netmap (deprecated, stil supported only for FreeBSD)
- PF_RING / PF_RING ZC (deprecated, available only for CentOS 6 in 1.2.0)
You can check out the comparison table for all available packet capture engines.
Official support groups:
- Mailing list
- Slack
- IRC: #fastnetmon at irc.libera.chat:6697 (TLS) web client
- Telegram: fastnetmon
- Discord: fastnetmon
Follow us at social media:
Complete integration with the following vendors
Features
- Detects DoS/DDoS in as little as 1-2 seconds
- Scales up to terabits on single server (sFlow, Netflow, IPFIX) or to 40G + in mirror mode
- Trigger block/notify script if an IP exceeds defined thresholds for packets/bytes/flows per second
- Complete support for most popular attack types
- Thresholds can be configured per-subnet basis with the hostgroups feature
- Email notifications about detected attack
- Complete IPv6 support
- Prometheus support: system metrics and total traffic counters
- Flow and packet export to Kafka in JSON and Protobuf format
- Announce blocked IPs via BGP to routers with ExaBGP or GoBGP (recommended)
- Full integration with InfluxDB and Graphite
- API
- Redis integration
- MongoDB protocol support compatible with native MongoDB and FerretDB
- VLAN untagging in mirror and sFlow modes
- Capture attack fingerprints in PCAP format
Running FastNetMon
Hardware requirements
- At least 1 GB of RAM
Installation
- Linux (Debian, CentOS, RHEL, Ubuntu), install instructions
- VyOS
- FreeBSD: official port.